Introduction
 Just a short blogpost about troubleshooting existing certificate services within the Active Directory domain. In this case the domain controllers were not able to renew their certificates through autoenrollment. In a meanwhile the existing certs were already expired so LDAPS was no longer available. A group of servers did not find any trouble updating their certs, so maybe it’s network related?
Just a short blogpost about troubleshooting existing certificate services within the Active Directory domain. In this case the domain controllers were not able to renew their certificates through autoenrollment. In a meanwhile the existing certs were already expired so LDAPS was no longer available. A group of servers did not find any trouble updating their certs, so maybe it’s network related?
Eventlogs
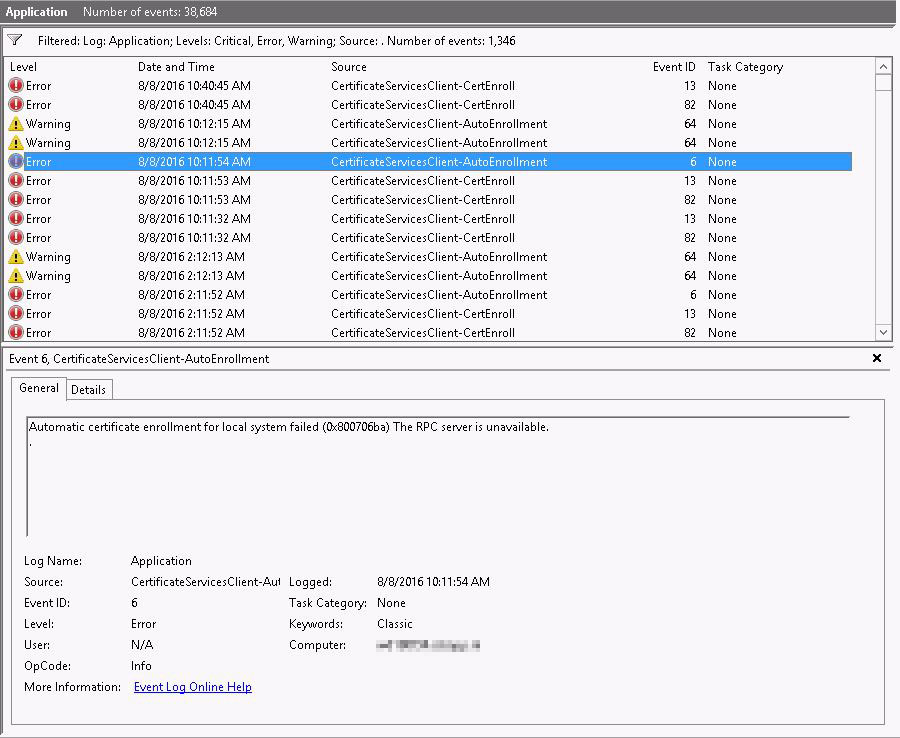
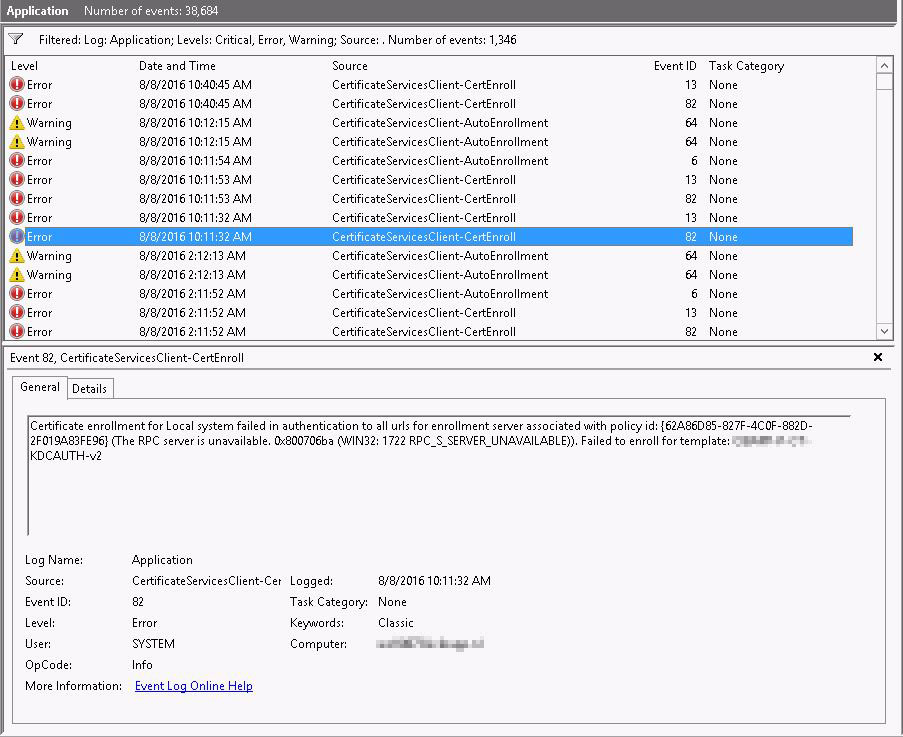
After checking the CA configuration I came to the conclusion that ADCS was functioning like it’s supposed to. Manually requesting a new cert from a working server was not a problem. The eventlogs of the domain controllers showed me a massive list of eventid 6 and 82. They desperately try to renew the cert but are failed.
Eventid 6: Automatic certificate enrollment for local system failed (0x800706ba) The RPC server is unavailable.
Eventid 82: Certificate enrollment for Local system failed in authentication to all urls for enrollment server associated with policy id: {62A86D85-827F-4C0F-882D-2F019A83FE96} (The RPC server is unavailable. 0x800706ba (WIN32: 1722 RPC_S_SERVER_UNAVAILABLE)). Failed to enroll for template KDCAUTH-v2
Troubleshooting
I tested connectivity between the domain controllers and de sub CA, everything was working except RPC traffic. As you can see from the events, RPC traffic is an issue. To test the path between the domain controller and de issuing CA use certutil -ping %caserver%. This attempts to contact the Active Directory Certificate Services Request interface.
In this case the high range RPC ephemeral ports were blocked at a firewall for the domain controller VLAN. This port range absolutely necessary for a correctly working Active Directory environment. The range is TCP & UDP 49152-65535. A lot of blogposts and other articles have been written about this subject because it’s not only Active Directory that depends on it, this is also the case for regular Windows servers and clients from Windows 2008/Vista and newer.